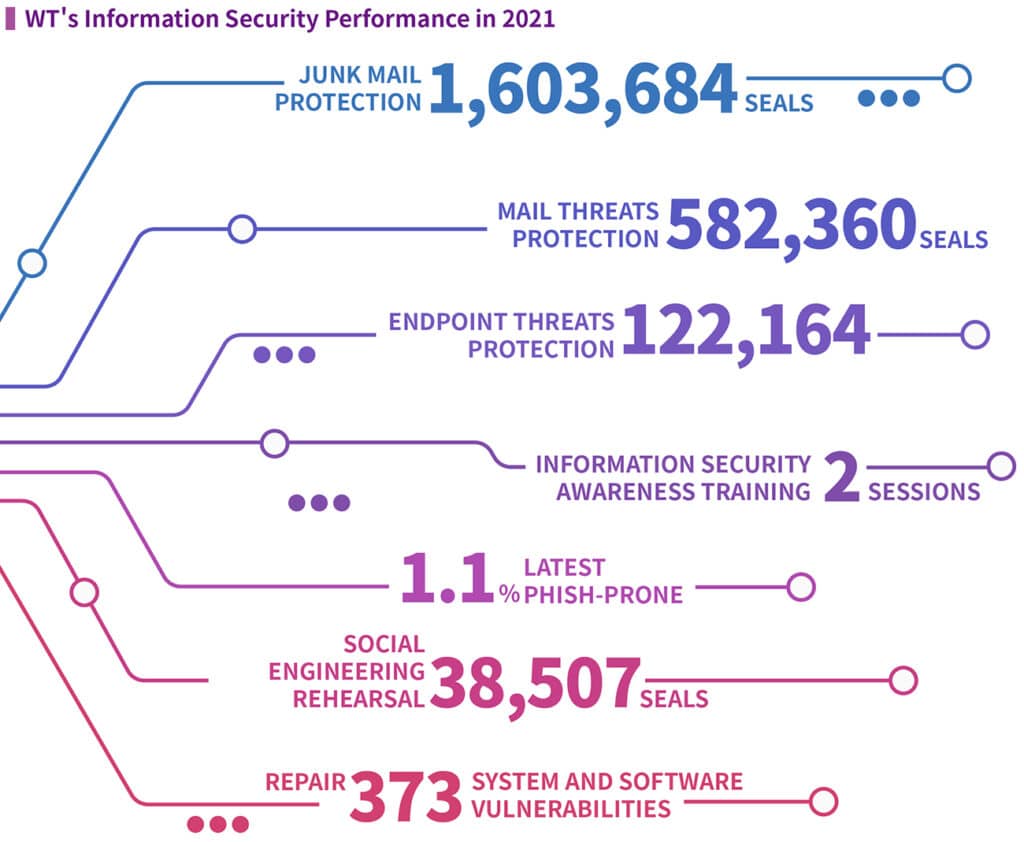
Enhancement of information security protection capacity
Becoming a Tier 1 operation
Delivering products to customers on time is the basis of WT’s operations, and system downtime will result in delayed delivery or the inability to deliver products. WT expects to become an enterprise with first-class operational capability in the industry, and a high degree of information security capability is the cornerstone for providing quality services. Third-party organizations such as international certifications and red team assessment are used to assist in the review. With enhanced information security protection and employee security awareness, no sensitive information was leaked in 2021, and there were no significant information service disruptions that caused financial losses to customers or suppliers’ operations.
Setting up a dedicated department to strengthen information security management
Because of information security’s increasing importance and proliferation of cyber-attacks, WT will set up a dedicated information security department in 2022. With a dedicated manager and two dedicated staff to focus on information security incident investigation, system vulnerability disclosure, and the assessment and implementation of new information security architecture. In addition, WT will evaluate the implementation of ISO 27001 to reduce the threat and impact of information security incidents through formalized and systematic control and management.
WT has set up dedicated emails to receive cyber security notifications from external customers, suppliers, the Taiwan Computer Network Crisis Management and Coordination Center (TWCERT), and information technology equipment and service vendors. WT has dedicated personnel to regularly collect information on major information security news, vulnerability disclosure, zero-day attacks, etc., to analyze, record, and set event levels. Internally, we set event levels according to severity while the information department records them. In case of a major information security incident, the Chief Operating Officer shall be notified immediately.
The information technology department must remediate and fix information security incidents within the target processing time and find the root cause, track and records the remediation and verify the effectiveness, and follows the PDCA method for continuous improvement to prevent the recurrence of incidents. In addition, WT classified information security incidents into several levels of severity and defined the recovery mechanisms and standard operating procedures to speed up the recovery point objective.
Build safety awareness among staff
The pandemic has swept through the world, changing people’s lifestyles and work styles. Working from home and remote work has become the norm. This causes employees to be detached from the protection of the corporate intranet and becomes a potential breach of corporate information security.
Strengthening employees’ security awareness has become an important part of information security. In the second half of 2021, WT introduced security awareness training and planned a basic phishing course and a discovery phishing game course. In 2021, 4,198 training sessions were completed (100% completion rate). Through video presentation and interactive teaching, we have enhanced our staff’s knowledge and awareness of information security and integrated security awareness into their daily work through continuous social engineering practices.


Backup and recovery plan in case of malicious intrusion
The Group has established comprehensive information security protection mechanisms. However, it cannot guarantee complete prevention from third-party attacks to crash the critical corporate system. When a severe attack occurs, the system may not be operational, leading to operational interruptions due to the inability to ship orders or compensation for customer losses due to shipment delays. Therefore, rapid system recovery is of the utmost importance. Apart from keeping investments in information security devices and software, The Company continually strengthens the system recovery mechanism.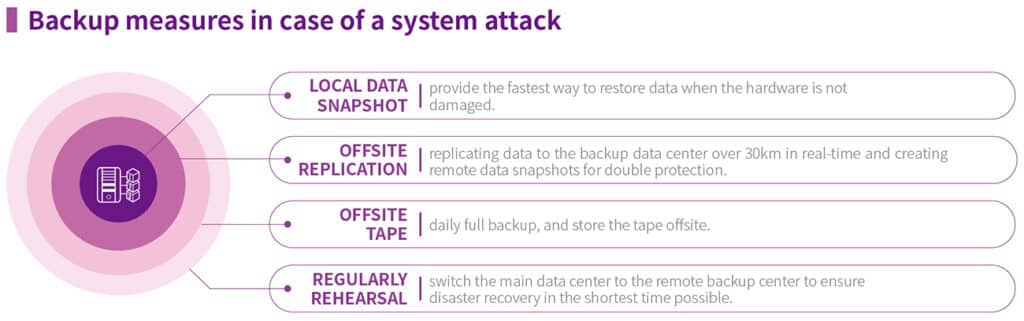
Introduction of the latest artificial intelligence NDR and EDR
Techniques for hack intrusions have been changing rapidly. In addition to exploiting the vulnerability and furthermore , hackers are using zero-day attacks to hack into systems before the patch. Hackers are also stealing employee accounts and passwords through phishing to gain direct access to the company’s system. Traditional pattern-matching protective measures no longer stop these numerous tactics.
WT introduced Network Detection Response (NDR) and Endpoint Detection Response (EDR) with an artificial intelligence machine learning mechanism in 2021. NDR performs front-line blocking and isolation when abnormal behavior deviation occurs on the network side. When the network side cannot identify and block in time and the threat enters the endpoint, the EDR mechanism blocks and isolates it again. Since there is no respite from network threats, we have also signed SOC/MDR services with third-party vendors to monitor information security threats 24/7.



